Best practices for ensuring customer data is secure and compliant with regulations while using Salesforce
Customer service today is more than just resolving issues — it is a trust-building function. Every interaction, whether through chat, phone, email, or online portals, involves the exchange of personal details. Customers expect companies to keep this information protected, accurate, and confidential.
But at the same time, customer service teams must work fast. They must respond quickly, understand context, view previous interactions, and sometimes access sensitive records to give complete support. This creates a challenging environment:

1. How can businesses deliver exceptional customer service while protecting customer data at every step?
In today’s digital-first world, the volume of customer data has grown significantly. Sensitive information — such as contact details, credit card information, addresses, health records, tickets, case notes, and user behaviour — travels across multiple systems. Companies must ensure that each system, including CRM, is secure and compliant with global regulations.
This is why businesses choose Salesforce. Salesforce provides a robust, secure, cloud-based environment with industry-leading protection measures, compliance certifications, and advanced features to safeguard customer data.
But the real security of Salesforce depends on:
- How the system is implemented
- How roles and permissions are designed
- How data is stored, accessed, and managed
- How organizations train their teams
- How automation and controls are applied
- How integrations are monitored
- How governance is enforced regularly
This is where Dhruvsoft plays a critical role. Dhruvsoft helps organizations implement Salesforce securely, set up compliance frameworks, and design customer service flows that follow global security standards. This article explains the reasons data security matters, Salesforce’s powerful built-in protections, best practices to follow, and Dhruvsoft’s strategic role in making your customer service operations both compliant and secure.
2. Why Data Security & Compliance Matter in Customer Service
Customer service teams handle the most confidential information in a business. This makes them a priority area for data protection and compliance.
2.1 Customer Trust and Brand Reputation
Trust is the foundation of every modern customer relationship. When customers contact support teams, they share sensitive information. They trust the brand to protect it. If this data is mishandled, it leads to:
- Loss of trust
- Public criticism
- Negative media coverage
- Drop in customer loyalty
- Reduced customer lifetime value
In fact, many studies show that customers switch brands immediately after a data breach—even if the service quality was good.
Protecting customer data is not only a compliance requirement but also a brand reputation strategy. A secure customer service system creates confidence and long-term retention.
2.2 Regulatory Pressures
Governments across the world are enforcing stricter data protection laws. Customer service operations must handle and store personal information in accordance with these regulations. Here are important regulations businesses need to follow:
GDPR (Europe) :
Applies to all companies handling data of EU residents. It requires:
- Consent tracking
- Data minimization
- Right to be forgotten
- Data access requests
- Secure storage and processing
CCPA (California)
Protects the data rights of California residents and requires companies to:
- Provide clear data usage information
- Allow customers to opt out
- Enable users to delete personal data
HIPAA (Healthcare – US)
Applies to hospitals, clinics, telemedicine providers, and health service organizations. Customer service teams must ensure:
- Secure handling of health records
- Protection of medical information
- Strong access controls
PCI-DSS (Global Payment Standard)
Customer service teams handling credit card data must follow:
- Secure storage
- Masking of card details
- Restricted access
- Secure communication
Penalties for Non-Compliance Include:
- Heavy fines (millions of dollars)
- Legal action
- Forced shutdown of operations
- Loss of customer confidence
- Damage to brand image
2.3 Internal Business Risks
Not all data risks come from external hackers. Many risks arise internally due to poor processes, lack of governance, or misuse.
Common internal risks include:
- Agents accessing data not meant for them
- Data being downloaded or exported without authorization
- Sensitive information stored in emails or spreadsheets
- Cases shared with users who should not view them
- Weak passwords or shared login credentials
- Lack of monitoring and auditing
Salesforce minimises these risks with strong role-based security, logging, tracking, and governance tools.
3. How Salesforce Ensures a Secure Customer Service Environment
Salesforce is considered one of the most secure CRM platforms globally. Its architecture is designed with multiple protective layers.
3.1 Salesforce’s Security-First Architecture
Salesforce operates on a multi-layered, multi-tenant cloud model. This means:
- Every customer’s data is isolated
- Data is separated logically
- High performance is maintained
- Constant security monitoring is in place
Salesforce has industry-grade security certifications such as:
- ISO 27001
- SOC 1
- SOC 2
- SOC 3
- PCI-DSS compliance for payment flows
- HIPAA compliance (with Salesforce Health Cloud)
This ensures that Salesforce meets the highest standards of global data security.
3.2 Data Encryption (At Rest & In Transit)
Salesforce uses strong encryption mechanisms:
- At Rest Encryption → Data stored on Salesforce servers is encrypted
- In Transit Encryption → Data moving between devices and Salesforce is encrypted
For organizations needing advanced protection, Salesforce Shield (an add-on feature) offers:
- Key management
- High-level encryption algorithms
- Encryption for custom fields
- Audit tracking of encrypted fields
This is critical for industries such as banking, finance, government, healthcare, and insurance.
3.3 Role-Based Access Controls (RBAC)
With RBAC Salesforce ensures that users only access what they need—nothing more.
Tools include:
- Profiles
- Roles
- Permission Sets
- Permission Set Groups
- Object-level access
- Field-level security
- Record-level control
RBAC ensures:
- Minimal data exposure
- Only authorized users view sensitive cases
- No accidental disclosure occurs
3.4 Audit Trails and Field History Tracking
Salesforce records:
- Every login attempt
- Every data view
- Every change made
- Every sensitive field update
- Every administrative action
This helps:
- Detect unusual behaviour
- Identify misuse
- Support compliance audits
- Maintain accountability
3.5 Secure Data Sharing Model
Salesforce defines data visibility through:
- Organization-Wide Defaults (OWD)
- Role hierarchies
- Sharing rules
- Manual sharing
- Team access
This allows companies to design very precise access patterns for service agents.
3.6 Salesforce Shield Features
Salesforce Shield (which can be purchased as an add-on), provides enterprise-grade compliance tools:
- Platform Encryption → To encrypt sensitive data
- Event Monitoring → Tracks real-time activity (downloads, exports, logins)
- Field Audit Trail → To track field history
This is essential for companies operating in regulated industries.
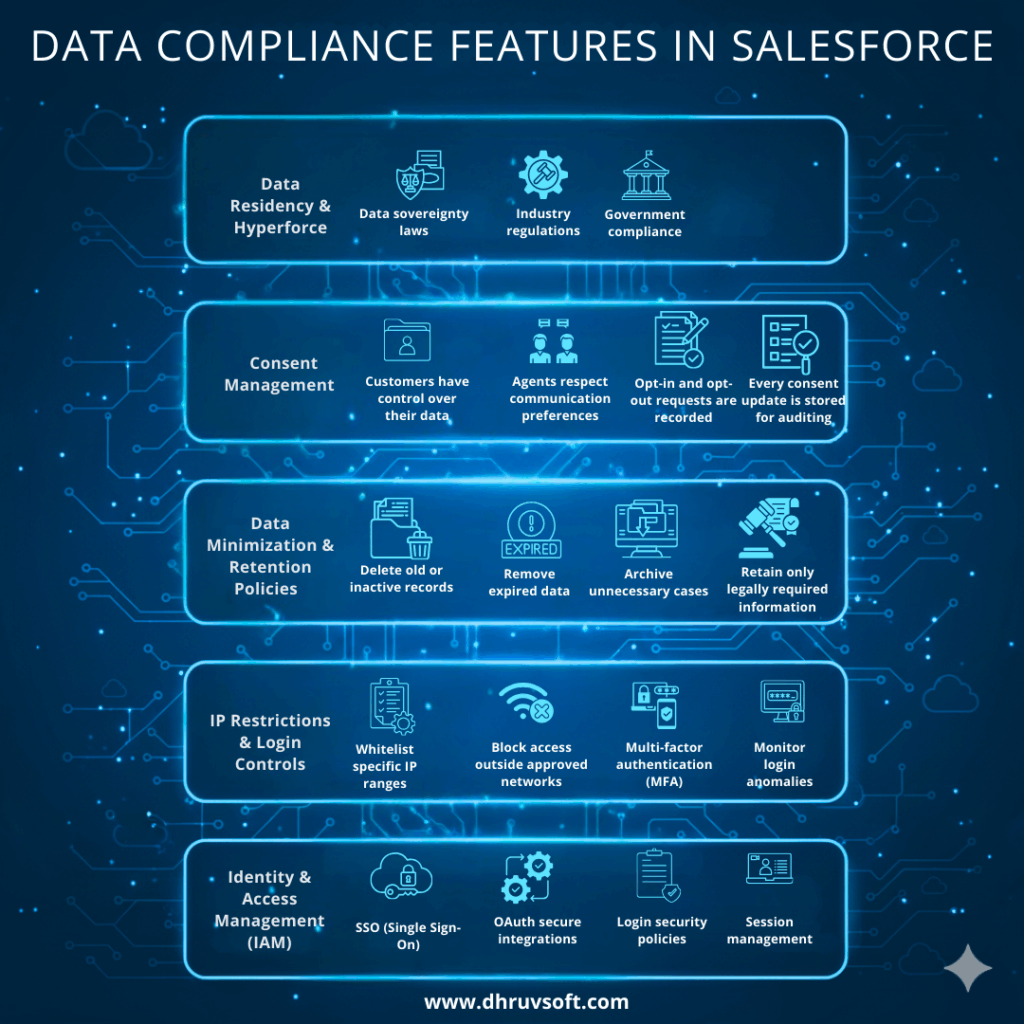
4. Data Compliance Features in Salesforce
4.1 Data Residency & Hyperforce
Many countries require data to be stored locally. Salesforce Hyperforce helps organizations host their data in specific regions, making it easier to meet:
- Data sovereignty laws
- Industry regulations
- Government compliance
4.2 Consent Management
Consent management ensures:
- Customers have control over their data
- Agents respect communication preferences
- Opt-in and opt-out requests are recorded
- Every consent update is stored for auditing
This is required for compliance with GDPR and CCPA.
4.3 Data Minimization & Retention Policies
Salesforce helps businesses:
- Delete old or inactive records
- Remove expired data
- Archive unnecessary cases
- Retain only legally required information
This reduces risk, storage costs, and compliance complexity.
4.4 IP Restrictions & Login Controls
Salesforce allows admins to:
- Whitelist specific IP ranges
- Block access outside approved networks
- Enforce multi-factor authentication (MFA)
- Monitor login anomalies
This reduces the risk of unauthorized access.
4.5 Identity & Access Management (IAM)
IAM tools include:
- SSO (Single Sign-On)
- OAuth secure integrations
- Login security policies
- MFA enforcement
- Session management
- Identity verification logs
These tools maintain a strong identity security layer.
5. Best Practices for Maintaining Data Security in Salesforce Customer Service
5.1 Implement Least Privilege Access
Users should only have the access they require. Providing broad permissions increases the risk of misuse.
Our team at Dhruvsoft can help you ensure:
- Minimum access
- Controlled field visibility
- Restricted case access
- Sensitive data availability only for authorized users
5.2 Conduct Regular Data Audits
Regular audits help detect:
- Unusual account activity
- Unauthorized access attempts
- Data downloads
- Case modifications
- High-risk user actions
Audits keep Salesforce healthy and compliant.
5.3 Keep Customer Data Clean & Updated
Data hygiene is important for:
- Accuracy
- Compliance
- Performance
Customer service teams must avoid storing:
- Expired information
- Duplicate profiles
- Sensitive documents in attachments
- Outdated conversations
5.4 Train Customer Service Teams Regularly
Human error is one of the biggest causes of data incidents.
Training topics should include:
- Data protection basics
- Identifying phishing emails
- Safe handling of customer documents
- Secure communication practices
- Role-based access discipline
- Steps to verify customer identity
5.5 Automate Compliance Workflows
Automation reduces mistakes. Salesforce can automate:
- Data anonymization
- Record deletion
- Consent renewal workflows
- Sensitive case access approvals
- Flagging high-risk activity
5.6 Use Case Management Securely
Use Salesforce features such as:
- Case teams
- Record types
- Region-based access
- Product-based segmentation
- Queue restrictions
This keeps sensitive cases restricted.
5.7 Secure All Integrations
Use:
- OAuth over username-password
- Encrypted API calls
- Approved apps
- Constant integration monitoring
Poor integrations create major exposure points.
6. Salesforce Security Tools for Customer Service Teams
6.1 Case-Level Security
Admins can:
- Restrict visibility of sensitive cases
- Limit cross-team access
- Prevent unauthorized case sharing
- Use case teams for controlled collaboration
6.2 ‘Knowledge Base’ Security
Knowledge articles can have different visibility levels:
- Internal only
- Customer community
- Public website
- Role-specific
Sensitive internal content should never be exposed externally.
6.3 Omni-Channel Data Protection
Omni-Channel ensures secure handling of:
- Chat
- Messaging apps
- Web-to-case
- Email-to-case
- Voice calls
Data from all channels is encrypted and logged.
6.4 Email-to-Case Security
Organizations must:
- Disable sensitive data transmission
- Filter suspicious emails
- Prevent attachment-based threats
- Route secure emails using verified channels
7. Dhruvsoft’s Role in Strengthening Salesforce Security & Compliance
7.1 Security-Focused Salesforce Implementation
Dhruvsoft configures:
- User roles
- Permission sets
- Role hierarchies
- Data access flows
- Case management rules
Implementation is done with a security-first mindset.
7.2 Compliance Consulting
Dhruvsoft helps businesses align Salesforce with:
- GDPR
- CCPA
- HIPAA
- PCI-DSS
- ISO 27001
- Internal IT policies
7.3 Security Audits & Health Checks
Our team evaluates:
- Hidden vulnerabilities
- Integration issues
- Admin access
- Data usage patterns
- Potential compliance gaps
7.4 Automation for Compliance
We can help you build automation for:
- Consent management
- Data retention controls
- Auto-anonymization
- Sensitive data access approval
- Audit-ready reports
7.5 Training Customer Service Teams
Training includes:
- Data handling
- Identifying threats
- Protecting sensitive information
- Avoiding common mistakes
- Using Salesforce securely
7.6 Managed Services & Continuous Support
Dhruvsoft provides:
- Continuous monitoring
- Regular security updates
- Configuration adjustments
- Compliance upgrades
- Ongoing governance
8. Common Mistakes Companies Make in Salesforce Data Security
Some frequent mistakes include:
- Too many users having admin access
- No MFA enforcement
- Storing sensitive files in attachments
- Exporting data to spreadsheets
- Not configuring IP restrictions
- Weak permission models
- Allowing unsecured third-party apps
- Ignoring login anomalies
- No regular training
- No audit logs review
Avoiding these mistakes greatly strengthens your security posture.
9. Conclusion
Customer service plays a central role in brand trust. Without strong data protection, even the best service experience loses value. In today’s digital landscape, customers expect companies to protect their personal information at every interaction.
Salesforce provides a secure, scalable, compliant platform that supports customer service teams with best-in-class security tools like encryption, RBAC, audit logs, Shield, IAM, consent management, and more.
But to unlock Salesforce’s full security potential, companies need expert guidance. Dhruvsoft helps businesses create a secure, compliant, and well-governed Salesforce environment by offering:
- Secure implementation
- Compliance consulting
- Detailed audits
- Automation frameworks
- Team training
- Ongoing governance
If you want a customer service setup that is secure, compliant, and trusted,
Connect with Dhruvsoft today and strengthen your Salesforce security framework.